The cloud appeal is undeniable. Agility, scalability, and cost-efficiency all beckon financial institutions (FIs) to migrate their data centers and applications to the cloud. However, for banks, security remains paramount.
According to Gartner, global spending on cloud solutions is projected to surge by 20.4% in 2024 alone. This explosive growth signifies a fundamental shift in how businesses operate.With this accelerating cloud adoption, financial leaders in banking and capital markets are shifting their perspectives on cloud computing. With a staggering 80% of the BFSI sector 📈 projected to be cloud-based by 2026, the Indian financial landscape is undergoing a rapid digital transformation.
Cloud computing has prompted a shift in business practices. Infrastructure has shifted from “static” to “dynamic” in terms of capacity and scale. Hardware, software, and access can be provisioned quickly with automation. The cost model has shifted from fixed to variable. Governance has changed from manual controls to automated ones. With so much already happening around, it is primarily important to look at the cloud from a security standpoint.
Here are some key security challenges banks must confront as they navigate the cloud landscape:
- Shared Responsibility Model in Cloud Security
- Legacy Systems and Applications
- Data Sensitivity and Data in Silios
- The Multi-Cloud Strategy
- The Insider Threat
- Difficulty Meeting Compliance Requirements
- Bridging the Skills Gap
1. Shared Responsibility Model in Cloud Security
The shared responsibility model in cloud computing delineates the security obligations between the cloud service provider (CSP) and the customer. This framework clarifies which entity is accountable for securing specific aspects of the cloud environment.
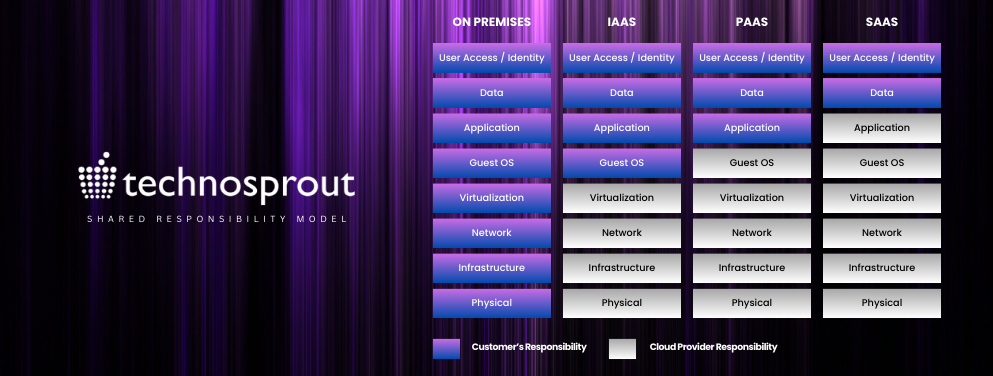
So as depicted above, no matter where you go Application, Access, and Data always remain the responsibility of a Consumer. These responsibilities constitute the “security in the cloud” aspect of the shared model.
Despite the prevalence of cloud data breaches (reported by 98% of businesses in the past 18 months), there is a concerning lack of understanding regarding cloud security responsibilities. Gartner predicts that by 2025, lack of talent or human failure will be responsible for over half of significant cyber incidents. A significant number of organizations mistakenly believe their CSP is solely responsible for data and application security. Closing this knowledge gap is crucial for organizations especially Banking institutions to fulfill their cloud security commitments and effectively mitigate security risks.
2. Legacy Systems and Applications
Unlike a fine wine, software applications don’t improve with age. While cherished friendships deepen over time, software becomes increasingly vulnerable and unreliable as the years go by. This presents a significant challenge for organizations, especially banks, that rely on legacy systems.
Challenges of Legacy Systems in the Cloud
Banks often find themselves entangled in a complex web of outdated security tools, many of which are ill-equipped to handle the dynamic nature of the cloud. These siloed systems create blind spots, hindering comprehensive threat detection and response. Here’s a closer look at some of the key challenges banks face when migrating legacy systems to the cloud:
- Security Vulnerabilities: Legacy systems often lack the robust security features of modern applications, making them more susceptible to cyberattacks.
- Inefficient Operations: Manual processes and outdated technologies can lead to cumbersome and inefficient workflows.
- Increased Maintenance Costs: Keeping legacy systems running requires ongoing maintenance and support, which can be expensive.
- Integration Challenges: Integrating legacy systems with modern cloud-based applications can be complex and time-consuming.
- Compliance Risks: Financial institutions must adhere to strict regulations, and legacy systems might not meet the latest compliance standards.
- Compatibility Issues: Legacy systems may not be compatible with new cloud technologies and platforms.
The Lift and Shift Fallacy
A common misconception is that migrating legacy systems to the cloud is a simple process of “lifting and shifting” them from on-premise environments. However, this approach often leads to friction, like trying to fit a square peg (legacy application) into a round hole (cloud environment). Legacy systems were not designed for the cloud’s dynamic and virtualized nature, and simply moving them can create new problems.
Shift Left Security: A Proactive Approach
A more secure and efficient approach involves “shifting left” security practices. This means embedding security considerations throughout the entire development lifecycle, not just as a final hurdle before deployment. Here’s how this approach helps with legacy application integration:
- Early Identification of Vulnerabilities: Security testing is integrated into the early stages of development, allowing teams to identify and address vulnerabilities before they become a problem.
- Secure Coding Practices: Developers are trained in secure coding practices to minimize the risk of introducing vulnerabilities during development.
- Continuous Monitoring: Legacy applications are continuously monitored for security threats and suspicious activity.
- Modernization Strategies for a Smooth Transition: While entirely replacing legacy systems might not always be feasible, there are strategies to ease the transition to the cloud like:
- Containerization: Containerization technologies like Docker can package legacy applications with their dependencies, making them more portable and easier to deploy in the cloud.
- API Gateways: API gateways can act as a single entry point for legacy applications, providing a more standardized and secure way to access them from the cloud.
By understanding the challenges and implementing these solutions, banks can successfully integrate legacy applications into the cloud and unlock the benefits of a hybrid cloud environment. This can lead to increased agility, scalability, and cost-efficiency while maintaining the robust security posture critical for the banking sector.
3. Data Sensitivity and Data in Silios
Today the world is data-driven, at least that is what is portrayed, but according to Harvard Business Review, Only about a quarter of organizations report that they are actually data-driven. Data is a lifeline for all financial institutions, However, critical information can become isolated within specific databases, applications, or departments, hindering effective data sharing across the organization. This phenomenon, known as data silos, arises from the fragmentation of data across various systems.
Compounding this challenge is the inherent sensitivity of financial data. Sensitive data refers to information, such as customer records or financial transactions, that requires strict confidentiality and access controls. Unauthorized access to such data can have significant consequences for both the institution and its customers.
List of Data that is considered Sensitive and Non-sensitive Data
| Sensitive PII | Non-sensitive PII |
| Bank account details | First and last names |
| Aadhaar Card Detail | Email addresses |
| Credentials and Cardholder Data | Mailing addresses |
| Passport Detail | Phone numbers |
| Other Financial Details | Social media profile names |
The Threat Landscape for Sensitive Data in Banks
Due to its high value, sensitive data held by financial institutions is a prime target for cybercriminals and adversaries. These actors seek financial gain or strategic advantage through the theft of sensitive data, posing a significant risk to organizations that host, store, or transmit such information.
Credential information, such as usernames and passwords, is a frequent target for hackers. Phishing scams and password-based attacks are common methods employed to gain unauthorized access. With successful credential theft, attackers can breach applications and systems to extract additional sensitive data or disrupt operations through denial-of-service (DoS) attacks or ransomware deployments.
The increasing use of cloud services by BFSI institutions, whether in full or hybrid models, introduces additional security concerns. Misconfigurations and user errors, often preventable, can lead to significant vulnerabilities. These human factors are attributed to 99% of cloud breaches, highlighting a critical issue when 36% of organizations store sensitive data in the cloud unencrypted
Security Measures for Protecting Sensitive Data in BFSI
To strengthen their cloud security and data management programs, BFSI organizations should consider implementing data security and data loss prevention (DLP) solutions alongside the following protective measures:
- Least Privilege Access: This principle minimizes access risks by restricting access to sensitive data and resources. Only authorized users with a legitimate need for specific data in order to perform their job duties should be granted access. Authentication mechanisms should be enforced to verify user identities.
- Data Encryption: Implementing company-wide encryption policies and providing software tools/ solutions for data encryption adds an additional layer of security. Encryption renders information unreadable to unauthorized users, even if a network breach occurs. This protects data “in motion” (during transfer), “in use” (while being processed), and “at rest” (when stored).
4. The Multi-Cloud Strategy
Many banks leverage multiple cloud providers for optimal flexibility and cost savings. While this approach offers benefits, it introduces a new layer of complexity – managing security across disparate cloud environments. Think of navigating a maze with different security measures at each turn. Consistency becomes paramount to avoid getting lost. One of the major issues here is :
- Increased architecture complexity: While staying with a single cloud provider offers familiarity and potentially lower initial costs, multi-cloud environments bring complexity. Managing multiple cloud platforms requires expertise in areas like networking, security, and data services across each provider. This can necessitate hiring specialists for each cloud, increasing overall expenses.
- Cloud Sprawl: Cloud sprawl happens when organizations create and forget about cloud resources. The ease of provisioning in the cloud can lead to a cluttered environment with unused or underused resources. This “sprawl” can significantly inflate cloud bills, impacting an organization’s bottom line. Effective cost management is essential to avoid this pitfall.
Managing complex multi-cloud environments requires more than just monitoring individual cloud provider tools. These tools offer limited visibility. Instead, organizations need a holistic view that provides actionable insights across the entire cloud ecosystem. This comprehensive perspective helps identify and resolve issues effectively, reducing frustration and bringing clarity to complex environments.

5. The Insider Threat
As digital systems become ever more sophisticated, so too does the risk of insider threats. Employees and third-party partners with authorized access can become unwitting pawns or even calculated attackers.
- Fortify Access Controls: Implement stringent measures to ensure that only authorized personnel can access sensitive systems and data. By implementing solutions like Role Based Access Management( RBAC), Just in time Access (JIT), and MFA(Multi-Factor Authentication), banking institutions can take measures to protect their organizations.
- Empower Employees: Conduct regular training on cybersecurity best practices, fostering a culture of awareness and vigilance.
Maintain Vigilance: Monitor user activity for anomalous behavior, allowing for timely detection and mitigation of potential insider threats.
6. Difficulty Meeting Compliance Requirements
Navigating regulations in the Banking sector is a constant tightrope walk. The rapid evolution of technology often outpaces the ability of regulators to adapt existing frameworks. This leaves institutions scrambling to stay compliant.
However, there’s hope. By embracing agility in their compliance strategies, Banking institutions can conquer this challenge:
- Adopting Compliance: Leverage technology to automate monitoring and reporting processes. This allows for continuous oversight and ensures regulations are met.
- Become Adaptable: Develop a culture of compliance that prioritizes flexibility. This allows for swift adjustments as regulations inevitably evolve.
By adopting these strategies, Banks can transform compliance from a burden to a strategic advantage, ensuring long-term success in an ever-changing landscape.

7. Bridging the Skills Gap
Security in the cloud goes beyond just securing systems. Banks need expertise in designing cloud architecture, managing workloads, and ensuring compliance across various environments. This often requires a skillset they might lack in-house. The cloud security skills gap remains a major challenge (94% of businesses rely on the public cloud). Here’s how CIOs can address it for 2024 and beyond:
- Automation & AI: Leverage automation and AI to handle routine tasks and threat detection, freeing up security teams.
- Training & Upskilling: Invest in training programs to equip existing employees with the necessary cloud security skills.
- Hiring External Talent: Consider hiring cloud security specialists or partnering with external providers to bridge the gap.
- Managed Security Providers (MSPs): Partner with MSPs for real-time threat detection and expertise in managing complex cloud environments.
Security Culture: Foster a culture of security awareness across the organization to empower employees to identify and report threats.
By implementing these strategies, organizations can navigate the evolving landscape of cloud security and effectively protect their critical assets.
How can we at Technosprout Help?
Amidst a myriad of MSSP options in the market and the skill gap, why opt for Technosprout? How can we help? What sets us apart?
Achieving cyber confidence begins with a solid strategy and governance. Technosprout leverages an “Assess, Design, Implement and Manage” four-pronged approach that leads organizations methodically through business transformation throughout the lifecycle.
Our managed security services provide customized, comprehensive solutions, addressing specific business needs strategically along with the best certified experts and an experience of 7+ years in the market.
Don’t let your organization be the next target. Empower your organization and secure your data. We help implement a Multi-Cloud Security Strategy, helping you protect your Application, Access, and Data.





