Remember the days when Cybersecurity was a cold dusty server room and cryptic warnings? Those days are gone. The constant evolution of businesses, be it daily, monthly, or annually, is mirrored in the ever-evolving challenges of cybersecurity. In fact, cybersecurity is no longer a singular concern, but rather a multifaceted landscape of threats. As these challenges have become more sophisticated, so too has the understanding of their complexities. Businesses have begun to recognize the need for a comprehensive approach to cybersecurity, and one of the most critical aspects of this strategy is ensuring the security of their cloud environments.
In 2023, a staggering 80% of organizations experienced at least one cloud security incident, highlighting the ever-present threat landscape. While the global cloud security market is expected to reach a colossal $62.4 billion by 2025, proactive investment in robust cloud defenses remains essential to safeguard your valuable data and prevent costly breaches. The message is clear “Elevate your business with right security investments, or face the peril of ignorance!“
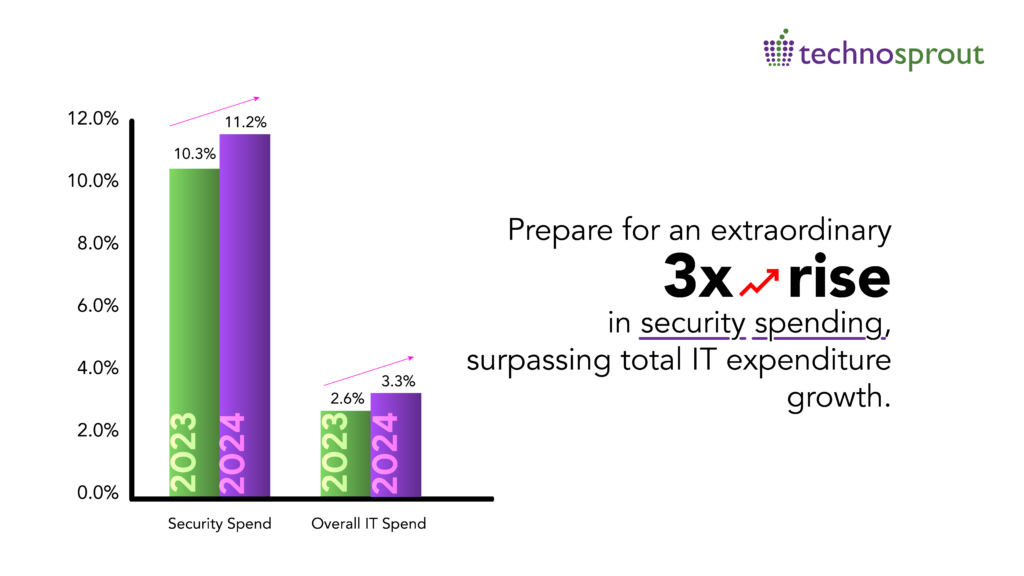
This brings us to an understanding that IT is a driver of productivity and Value – not a cost center. Consider Cloud Security as a Business Investment for Better Outcomes. A Gartner survey states that 88% of the board of directors also believe that cloud security is more of a business issue, more than a technical one. Therefore it’s important to invest in outcomes rather than tools. It is necessary to align protection levels with desired business outcomes to drive business-led cloud security investment.
Therefore dear ‘C-suite’s it’s first and foremost important for you to understand your responsibility and at the same time be able to communicate the risks, value and cost of cloud security to your board of directors.
While a silver bullet for organizational cybersecurity doesn’t exist, there are effective strategies every company can consider. To equip you with a starting point, we’ve outlined several key areas to focus on.
Know Yourself: The Foundation of Cloud Security Strategy
The starting point for any effective Cloud Security strategy is a deep understanding of the organization itself. What is the mission and vision? What risks is the organization willing to take? What’s the acceptable duration of unplanned downtime?
Cloud security measures are fundamentally about protecting an organization’s viability. Therefore, a strategy should be built around identifying and securing sensitive assets & data, conducting a thorough risk and impact analysis and formulating contingency plans. Factors such as company size, specialization, resources and legal obligations also play a crucial role in shaping an effective strategy.
Employees your First Line of Defense
Your cloud security strategy is only as strong as its weakest link, and often, that link is human. Employees play a pivotal role and should not be overlooked. Regardless of the sophistication of security measures, if employees are not trained and aware of security concerns, efforts may be in vain.
To fortify this human firewall, organizations must invest in comprehensive employee training, raising awareness about potential threats, and emphasizing the importance of corporate procedures in maintaining system safety. In short, Identity & Access Management will also play a vital role in strategically aligning your security because after all Hackers do not just hack in they log in!
Human Identity is just the tip of Iceberg
“Securing Human Identities is like securing the front door of your house, but without securing Machine Identities, it’s like leaving the back door wide open.“
Machines are increasingly interconnected, managing sensitive data and performing critical tasks. Each device has an identity that needs protection. That’s where machine-to-machine (M2M) identity comes in.
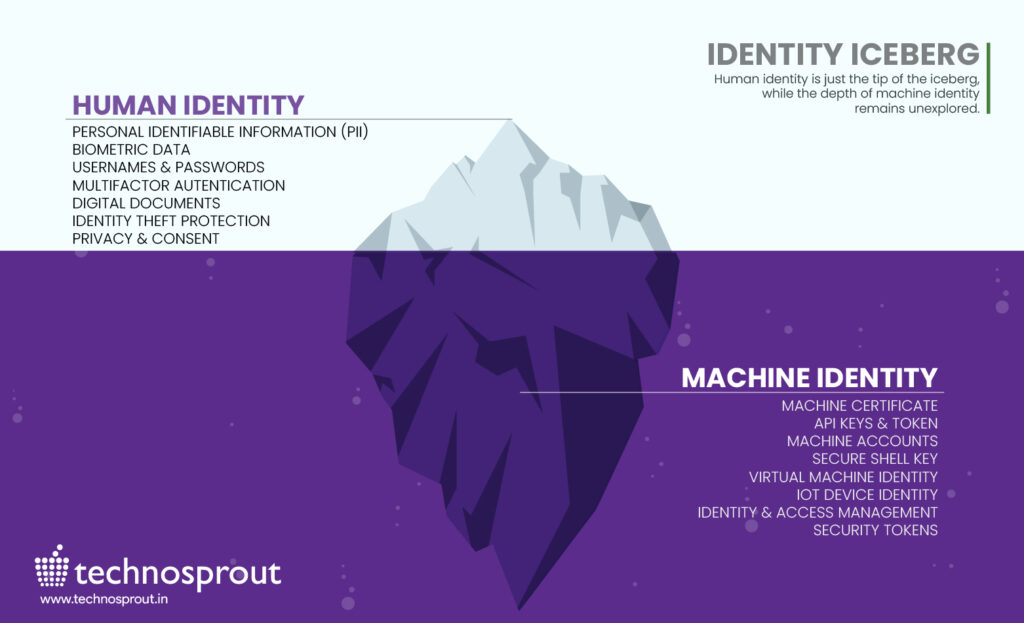
A recent study by Ponemon Institute revealed that compromised M2M devices cost businesses an average of $5.4 million per incident, highlighting the critical need for robust M2M security measures.
Unsecured M2M identities can become gateways for attackers, providing a backdoor into your network. Robust M2M Identity management ensures that only authorized devices connect, access data and execute commands. Think of it as extending your human firewall to the machine ecosystem, creating a comprehensive defense against evolving threats.
Fortify your M2M security with technologies like Public Key Infrastructure (PKI) for issuing and managing machine identities and zero-trust principles for verifying every device and connection before granting access.
Application Almost Powers Everything!
Applications are the lifeblood of businesses. From customer interactions to internal operations, everything relies on their smooth and secure functioning. That’s why application security is no longer optional – it’s fundamental.
Think of it like protecting your castle. Even a small narrow opening in the wall can be exploited by attackers and with applications, even minor vulnerabilities can be combined to create major breaches. Application security proactively identifies and addresses these weak spots, minimizing the attack surface and making it much harder for intruders to gain a foothold.
It’s a shift from waiting for an attack to happen and then scrambling to fix it, to a smarter, more strategic approach. Imagine nipping security issues in the bud before they have a chance to disrupt your operations or harm your customers. Proactive application security gives you that edge, potentially saving you time, money and reputational damage. It’s the security equivalent of a well-maintained moat and fortified walls – a proactive defense that gives you peace of mind and keeps your castle safe.
Investing in the right tool
While foundational security tools are crucial, the real power lies in selecting solutions that seamlessly integrate with your organization’s unique security landscape. This tailored approach ensures your defenses effectively address your specific vulnerabilities and threats. Specialized expertise is necessary for effective analysis, planning and implementation of security measures. Many organizations, irrespective of size, opt for managed services to ensure they have the right tools in place.
The evolving threat landscape demands a shift in perspective—from viewing cloud security as a cost center to recognizing it as a strategic advantage. By aligning security measures with organizational objectives, investing in employee training, protecting application identity and data and selecting the right tools, businesses can position cloud security as a valuable asset in the journey toward long-term success. Embrace this paradigm shift, fortify your organization, and navigate the complexities of the digital age with resilience.
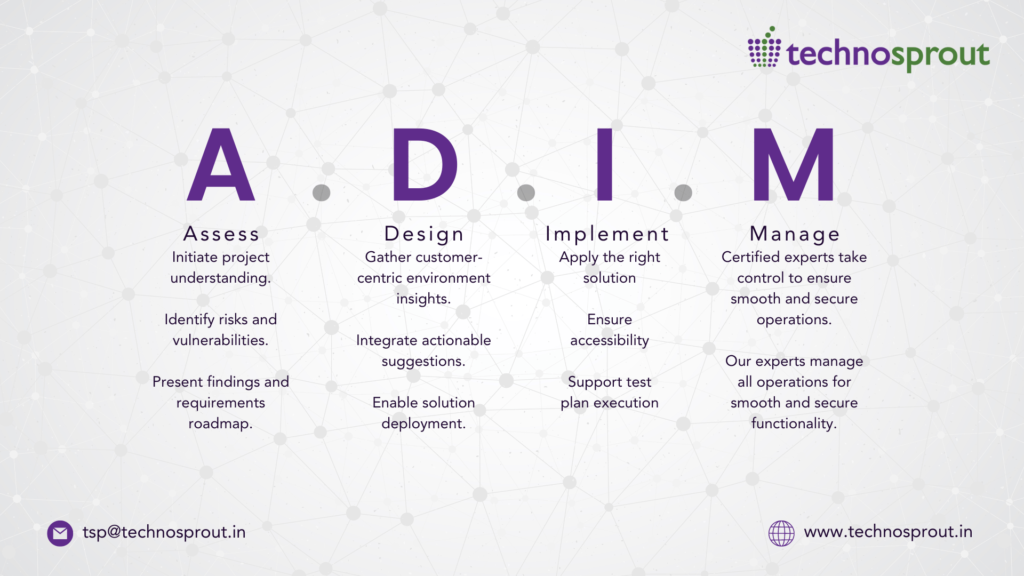
Technosprout leverages an “Assess, Design, Implement and Manage” four-pronged approach that leads organizations methodically through business transformation, encompassing partnership with Gartner leading solutions ensuring that your organization remains on the top of the cloud security curve. Let’s get in touch and explore opportunities and together enhance your Security strategy.
Ready to leverage Technosprout’s expertise and experience to secure your organization? Watch our corporate video for a comprehensive overview of our solutions and services, and learn how we can help you build a robust cybersecurity strategy.





